28 Sep FORESIGHT: Towards a sustainable exploitation of the project results
The objective of the FORESIGHT project is to raise the number of talented cyber-security professionals at all levels by providing a platform that enhances the capabilities of existing cyber ranges. The objective arose from the increasing number of cyber-attacks among different domains such as aviation, naval and power-grid environments. With the end of the project approaching, it is important to determine how the results will be used beyond the project duration in order to have a sustainable impact. In this context, work is done in close cooperation with the project partners in order to meet the needs of everyone involved in the project.
Need for cyber-security solutions
Attacks on critical infrastructure such as naval, maritime and energy sectors have been rapidly growing in the recent past. Attacks are not only increasing in physical nature, but also in the cyber-sphere, and these realms are often interconnected. The increasing number of attacks shows that the topic of cyber-security is becoming more and more relevant. Not only for governments, critical infrastructure companies and businesses but also for ordinary citizens. Yet the problem is that the various stakeholders are not well enough prepared for the growing threat. There is a lack of resources, both infrastructural and human. Especially in the critical infrastructure sector such as naval, power grid and maritime, it is important that cyber-attacks are prevented and if they do occur, that they are remedied as quickly as possible. Currently, companies are lacking in various areas that are important for preventing and responding to cyber-attacks. These shortcomings range from a lack of situational awareness about possible attacks and inadequate measures for preventing and dealing with cyber-attacks, to a lack of professionally trained personnel.
Exploitation management
Precisely to address these prevailing deficiencies mentioned above, the results developed within the FORESIGHT project are of utmost relevance. The FORESIGHT platform provides a solution to train personnel in critical infrastructure environments such as the naval, maritime and energy sectors in cyber-security. Hence, the platform enables improved organisational preparedness for possible cyber-attacks at all levels.
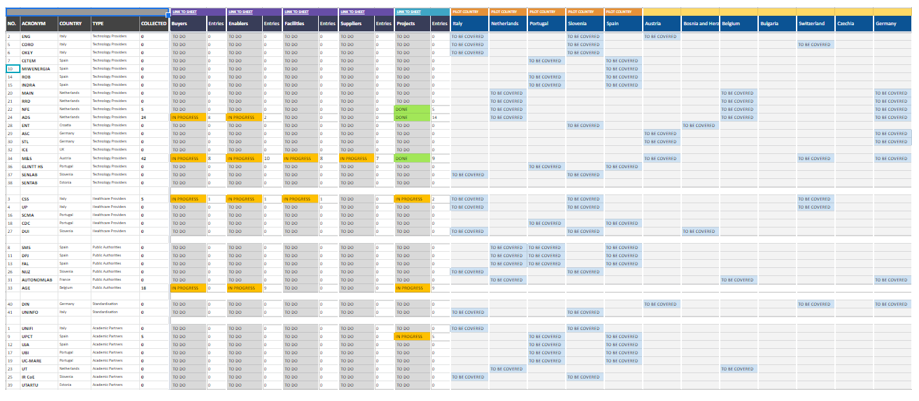
With the progressing development of the FORESIGHT project, the focus shifted from the development of project results to the exploitation of the results. The exploitation of project results is a very complex process, as many aspects have to be considered and discussed and some critical choices have to be made. Since the results have been developed in cooperation with all partners, the decision on the exploitation of the results also needs to be made jointly in the consortium. The role of coordinating exploitation management is taken over by MINDS & SPARKS GmbH.
Questionnaire structure
For the exploitation of project results, it is important to clarify which results are going to be exploited, how they are going to be exploited, and who wants to claim the rights to the results after the end of the project. For this purpose, a questionnaire was created, which will be jointly completed by all consortium partners. An overview of the aspects covered by the survey is listed in the following:
- Individual exploitation plans: The partners must answer questions regarding their individual exploitation plans. In particular, about which results they are planning to exploit, in which market sectors, via which channels, what the expected sales are and which exploitation goals have already been achieved.
- Exploitable result prioritization: To create business plans, the most promising outcomes of the project must be selected. For this purpose, a prioritisation of the results is conducted and the partners must provide a rating for each result in terms of innovation, exploitability and impact on the industry.
- Exploitation routes: During the project, several exploitation routes have already been presented. These include commercial exploitation, educational exploitation, scientific exploitation and exploitation by/through networks, associations, initiatives and policy groups. For each result, the partners must specify which route they think is the most promising. The answers will frame the preparation of the business plans.
- IPR management: IPR management is another important aspect that needs to be clarified. On the one hand, to protect the project results, on the other hand, the rights and privileges are only clearly defined during the project duration, but not beyond. Therefore, several questions need to be answered by the partners. This includes whether they have contributed to the results, what they consider most useful for protection (for example, patents), and whether they are interested in claiming the rights.
- Value proposition: In addition to the exploitation-specific questions, there is a question about FORESIGHT’s value proposition. For this, the partners have to answer various questions on the areas of customer profile and value map.
Through the questionnaire, we will get valuable responses to drive the exploitation of results in the project. By prioritising the results and evaluating the exploitation routes, the basis for exploiting the results is already set. As a result, we can focus on the most important results and, if needed, create specific business plans for them. Furthermore, we will receive important answers from the partners for the IPR management and can use them to create an overview through an IPR matrix. This allows us to see for each result which partners have contributed to it, how it should be protected, who claims the rights to it, and for what purpose the rights are claimed. With the help of this matrix, potential overlaps, for example, if two partners claim the rights for the same result, can be identified and a workshop can be initiated with the respective partners to find a common solution.
https://twitter.com/FORESIGHT_H2020
https://www.linkedin.com/groups/8865069/
https://www.youtube.com/channel/UCXwhbVlSHaS7i3srzSKNDXw/
Cyber-range, cyber-security, preparedness, security training, threats, organisations, exploitation, IPR,