05 Nov GUARD: Human implications for the user interface
Within the GUARD project, a user interface (UI) that aims to increase situational cybersecurity awareness has to be implemented. Since humans are in the centre of digital service chains, it is essential to develop an UI that adapts to human needs. To this end, a comprehensive literature research was carried out, focusing on behavioural, social and human aspects. Also, the project collected preliminary inputs from end users on typical user roles that were used to derive recommendations for the UI.
The GUARD project created a dashboard that presents cybersecurity threats and weaknesses of the corresponding digital service chains at a glance. This task is directly linked to the main project objective – developing an open and extensible platform for advanced assurance and protection of trustworthy and reliable business chains spanning multiple administrative domains and heterogeneous infrastructures.
The vulnerability of modern digital systems to cybersecurity breaches is steadily increasing as these systems become more complex. Due to the high level of human involvement, it is no longer practical and satisfactory to rely solely on manual operation, configuration, and management. Therefore, it is critical to assess the function and impact of humans on complex information and communication technology (ICT) systems. Regarding the human implications, GUARD aspires to improve situational awareness by comprehensively disseminating knowledge to the people involved in different levels of the organisation. This is to be achieved through tailored content that enables a quick and effective response to cyber threats and prevents inertia when sharing information about new threats and attacks. To achieve this goal, the project partners carried out an analysis that shows how effective interaction can be achieved through a modern security UI that enhances usability.
The following four essential aspects could be defined as the main results of the analysis and should, in any case, be considered when creating an UI:
- Humans lack the ability to process big data [1].
- Raising awareness about security and privacy conflicts with the useability of a UI. Complex security damages useability and vice versa [2] [3].
- It is not expected that users are able to maintain vigilant, patient and aware of security issues [4].
- Oftentimes, researchers only focus on the “ideal” user and fail to take into account users affected by limitations [5].
Web interface design principles
The GUARD web interface must incorporate design ideas that address a wide range of human, behavioural, and social elements. For a good user experience, the most important information must be available at a glance. This should support the user in adjusting his or her behaviour and making an appropriate decision. The main objective of a cybersecurity interface is to assist the user in completing tasks, solving problems and obtaining answers to inquiries. The requirements for the UI have resulted in several design principles that should equally be considered when developing the UI.
Data visualisation
One of the most important aspects of a successful interface implementation is the capacity to clearly communicate information about cyber security issues to the end user. The GUARD interface design aims to raise situational awareness. To reach this objective, a compact, concise presentation of a large amount of data is required. This data must allow the user to identify circumstances that require an operational or strategic response. Typical scenarios of detecting or responding to a cyber security event are usually time-critical and stressful, which is why the volume of underlying data often exceeds the amount that can be processed by a human. Data visualisations can address this problem by compiling the data in a human-readable form. Examples of possible data visualisations are pie charts, doughnut charts, bar charts, line graphs, or map visualisations.
User engagement
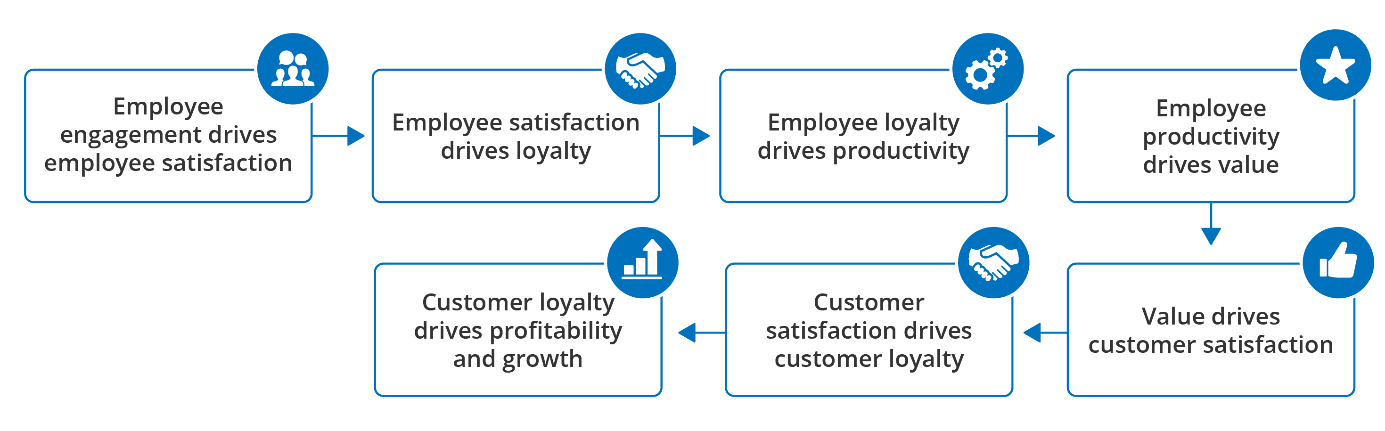
User engagement is a crucial design principle that also needs to be considered. Applying appropriate strategies and models ensures user retention, feeds user satisfaction and consequently boosts commitment and productivity. The “Service-Profit Chain” [6] underlines the importance of user engagement when designing a web interface.
Human limitations
When building a web interface, it is recommended to consider human limitations. These limitations can be classified as cognitive limitations (e.g., reduced attention, concentration or memory issues) or limitations related to impairments (e.g., motor disability, vision disability, etc.). To develop an inclusive UI, all limitations have to be taken into account. Suitable solutions are already available for each of the presented limitations.
Conclusion
To develop an UI for the GUARD framework that is both efficient and suitable for cyber-security-related issues, various factors have to be considered. The analysis carried out by the project partners points out which aspects need to be considered regarding human implications in order to create an adequate cyber security dashboard. The next step is to make recommendations based on the results of the analysis. These recommendations are then used as input for the creation of the UI.